|
Z-BLOG后台利用插件拿WEBSHELL
怎么进后台自己想办法,进入后台
插件管理--TotoroⅡ插件,导出此插件,下载本地利用文本形式打开
base64加密的
PCVAIENPREVQQUdFPTY1MDAxICU+DQo8JQ0KJy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8v
Ly8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8N
CicvLyDmj5Lku7blupTnlKg6ICAgIFotQmxvZyAxLjcNCicvLyDmj5Lku7bliLbkvZw6ICAg
IA0KJy8vIOWkhyAgICDms6g6ICAgIA0KJy8vIOacgOWQjuS/ruaUue+8miAgIA0KJy8vIOac
gOWQjueJiOacrDogICAgDQonLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8v
Ly8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLy8vLw0KJT4NCjwlIE9w
dGlvbiBFeHBsaWNpdCAlPg0KPCUgT24gRXJyb3IgUmVzdW1lIE5leHQgJT4NCjwlIFJlc3Bv
bnNlLkNoYXJzZXQ9IlVURi04IiAlPg0KPCUgUmVzcG9uc2UuQnVmZmVyPVRydWUgJT4NCjwh
LS0gI2luY2x1ZGUgZmlsZT0iLi4vLi4vY19vcHRpb24uYXNwIiAtLT4NCjwhLS0gI2luY2x1
ZGUgZmlsZT0iLi4vLi4vZnVuY3Rpb24vY19mdW5jdGlvbi5hc3AiIC0tPg0KPCEtLSAjaW5j
bHVkZSBmaWxlPSIuLi8uLi9mdW5jdGlvbi9jX2Z1bmN0aW9uX21kNS5hc3AiIC0tPg0KPCEt
LSAjaW5jbHVkZSBmaWxlPSIuLi8uLi9mdW5jdGlvbi9jX3N5c3RlbV9saWIuYXNwIiAtLT4N
CjwhLS0gI2luY2x1ZGUgZmlsZT0iLi4vLi4vZnVuY3Rpb24vY19zeXN0ZW1fYmFzZS5hc3Ai
IC0tPg0KPCEtLSAjaW5jbHVkZSBmaWxlPSIuLi8uLi9mdW5jdGlvbi9jX3N5c3RlbV9ldmVu
dC5hc3AiIC0tPg0KPCEtLSAjaW5jbHVkZSBmaWxlPSIuLi8uLi9mdW5jdGlvbi9jX3N5c3Rl
bV9wbHVnaW4uYXNwIiAtLT4NCjwhLS0gI2luY2x1ZGUgZmlsZT0iLi4vLi4vcGx1Z2luL3Bf
Y29uZmlnLmFzcCIgLS0+DQo8JQ0KDQpDYWxsIFN5c3RlbV9Jbml0aWFsaXplKCkNCg0KJ+aj
gOafpemdnuazlemTvuaOpQ0KQ2FsbCBDaGVja1JlZmVyZW5jZSgiIikNCg0KJ+ajgOafpead
g+mZkA0KSWYgQmxvZ1VzZXIuTGV2ZWw+MSBUaGVuIENhbGwgU2hvd0Vycm9yKDYpIA0KDQpJ
ZiBDaGVja1BsdWdpblN0YXRlKCJUb3Rvcm8iKT1GYWxzZSBUaGVuIENhbGwgU2hvd0Vycm9y
KDQ4KQ0KJT4NCjwlDQoNCkRpbSBhY3QsZGVsaWQNCmFjdD1SZXF1ZXN0LkZvcm0oImFjdCIp
DQpkZWxpZD1SZXF1ZXN0LkZvcm0oImlkIikNCkRpbSBzdHJDb250ZW50DQpEaW0gc3RyWkNf
VE9UT1JPX0JBRFdPUkRfTElTVCxTdHJUTVAsTkVXX0JBRFdPUkQsYm9sVE9UT1JPX0RFTF9E
SVJFQ1RMWQ0Kc3RyQ29udGVudD1Mb2FkRnJvbUZpbGUoQmxvZ1BhdGggJiAiL1BMVUdJTi90
b3Rvcm8vaW5jbHVkZS5hc3AiLCJ1dGYtOCIpDQpDYWxsIExvYWRWYWx1ZUZvclNldHRpbmco
c3RyQ29udGVudCxUcnVlLCJTdHJpbmciLCJUT1RPUk9fQkFEV09SRF9MSVNUIixzdHJaQ19U
T1RPUk9fQkFEV09SRF9MSVNUKQ0KQ2FsbCBMb2FkVmFsdWVGb3JTZXR0aW5nKHN0ckNvbnRl
bnQsVHJ1ZSwiQm9vbGVhbiIsIlRPVE9ST19ERUxfRElSRUNUTFkiLGJvbFRPVE9ST19ERUxf
RElSRUNUTFkpDQpJZiBhY3Q9ImRlbGNtIiB0aGVuDQoNCglEaW0gb2JqQ29tbWVudA0KCVNl
dCBvYmpDb21tZW50PU5ldyBUQ29tbWVudA0KCUlmIG9iakNvbW1lbnQuTG9hZEluZm9ieUlE
KGRlbGlkKSBUaGVuDQoJDQoJCVN0clRNUD1UT1RPUk9fY2hlY2tTdHIob2JqQ29tbWVudC5I
b21lUGFnZSAmICJ8IiAmIG9iakNvbW1lbnQuQ29udGVudCxzdHJaQ19UT1RPUk9fQkFEV09S
RF9MSVNUKQ0KCQlzdHJaQ19UT1RPUk9fQkFEV09SRF9MSVNUPXN0clpDX1RPVE9ST19CQURX
T1JEX0xJU1QgJiBTdHJUTVANCgkJTkVXX0JBRFdPUkQ9U3RyVE1QDQoJCVJlc3BvbnNlLldy
aXRlIFRvdG9yb19kZWFsSXQob2JqQ29tbWVudCxib2xUT1RPUk9fREVMX0RJUkVDVExZKQ0K
DQoJRW5kIElmCQkNCgkJDQpFbHNlaWYgYWN0PSJkZWx0YiIgdGhlbg0KDQoJRGltIG9ialRy
YWNrQmFjaw0KCVNldCBvYmpUcmFja0JhY2s9TmV3IFRUcmFja0JhY2sNCglJZiBvYmpUcmFj
a0JhY2suTG9hZEluZm9ieUlEKGRlbGlkKSBUaGVuDQoJDQoJCVN0clRNUD1UT1RPUk9fY2hl
Y2tTdHIob2JqVHJhY2tCYWNrLlVSTCAmICJ8IiAmIG9ialRyYWNrQmFjay5FeGNlcnB0LHN0
clpDX1RPVE9ST19CQURXT1JEX0xJU1QpDQoJCXN0clpDX1RPVE9ST19CQURXT1JEX0xJU1Q9
c3RyWkNfVE9UT1JPX0JBRFdPUkRfTElTVCAmIFN0clRNUA0KCQlORVdfQkFEV09SRD1TdHJU
TVANCgkJUmVzcG9uc2UuV3JpdGUgVG90b3JvX2RlYWxJdChvYmpUcmFja0JhY2ssYm9sVE9U
T1JPX0RFTF9ESVJFQ1RMWSkNCgkNCglFbmQgSWYNCgkNCkVuZCBJZg0KDQpJZiBsZWZ0KHN0
clpDX1RPVE9ST19CQURXT1JEX0xJU1QsMSk9InwiIHRoZW4gc3RyWkNfVE9UT1JPX0JBRFdP
UkRfTElTVD1SaWdodChzdHJaQ19UT1RPUk9fQkFEV09SRF9MSVNULCBMZW4oc3RyWkNfVE9U
T1JPX0JBRFdPUkRfTElTVCkgLSAxKQ0KQ2FsbCBTYXZlVmFsdWVGb3JTZXR0aW5nKHN0ckNv
bnRlbnQsVHJ1ZSwiU3RyaW5nIiwiVE9UT1JPX0JBRFdPUkRfTElTVCIsc3RyWkNfVE9UT1JP
X0JBRFdPUkRfTElTVCkNCkNhbGwgU2F2ZVRvRmlsZShCbG9nUGF0aCAmICIvUExVR0lOL3Rv
dG9yby9pbmNsdWRlLmFzcCIsc3RyQ29udGVudCwidXRmLTgiLEZhbHNlKQ0KJ0lmIE5FV19C
QURXT1JEPD4iIiBUaGVuIFJlc3BvbnNlLndyaXRlICIsVG90b3Jv4oWh5paw5aKe5LiL5YiX
6buR6K+N77yaICIgJiBSaWdodChORVdfQkFEV09SRCwgTGVuKE5FV19CQURXT1JEKSAtIDEp
DQoNCiU+DQo8JQ0KRnVuY3Rpb24gVE9UT1JPX2NoZWNrU3RyKHN0clRvQ2hlY2ssQkFEV09S
RF9MSVNUKQ0KCQlEaW0gb2JqUmVnLG9iak1hdGNoZXMsTWF0Y2gNCgkJU2V0IG9ialJlZyA9
IE5ldyBSZWdFeHANCgkJb2JqUmVnLklnbm9yZUNhc2UgPSBUcnVlDQoJCW9ialJlZy5HbG9i
YWwgPSBUcnVlDQoJCW9ialJlZy5QYXR0ZXJuID0gImh0dHA6Ly8oW1x3LV0rXC4pK1tcdy1d
KyINCgkJU2V0IG9iak1hdGNoZXMgPSBvYmpSZWcuRXhlY3V0ZShzdHJUb0NoZWNrKQ0KCQlG
b3IgRWFjaCBNYXRjaCBJbiBvYmpNYXRjaGVzDQoJCQlJZiBUb3Rvcm9fY2hlY2tOZXdCYWRX
b3JkKE1hdGNoLlZhbHVlLEJBRFdPUkRfTElTVCAmIFRPVE9ST19jaGVja1N0cikgdGhlbg0K
CQkJCVRPVE9ST19jaGVja1N0cj1UT1RPUk9fY2hlY2tTdHIgJiAifCIgJiBSaWdodChNYXRj
aC5WYWx1ZSwgTGVuKE1hdGNoLlZhbHVlKSAtIDcpDQoJCQlFbmQgaWYNCgkJTmV4dA0KCQlT
ZXQgb2JqUmVnID0gTm90aGluZw0KCQlTZXQgb2JqTWF0Y2hlcyA9IE5vdGhpbmcNCgkJU2V0
IE1hdGNoID0gTm90aGluZw0KRW5kIEZ1bmN0aW9uDQoNCkZ1bmN0aW9uIFRvdG9yb19jaGVj
a05ld0JhZFdvcmQoY29udGVudCxCQURXT1JEX0xJU1QpDQoNCglUb3Rvcm9fY2hlY2tOZXdC
YWRXb3JkPVRydWUNCglEaW0gaSxqDQoJaj0wDQogICAgRGltIHN0ckZpbHRlcg0KICAgIHN0
ckZpbHRlciA9IFNwbGl0KEJBRFdPUkRfTElTVCwgInwiKQ0KCUZvciBpID0gMCBUbyBVQm91
bmQoc3RyRmlsdGVyKQ0KCQlJZiBzdHJGaWx0ZXIoaSk8PiIiIFRoZW4NCgkJCUlmIEluU3Ry
IChMQ2FzZShjb250ZW50KSwgTENhc2Uoc3RyRmlsdGVyKGkpKSkgPiAwIFRoZW4NCgkJCQlU
b3Rvcm9fY2hlY2tOZXdCYWRXb3JkPUZhbHNlDQoJCQkJRXhpdCBGb3INCgkJCUVuZCBJZg0K
CQlFbmQgSWYNCiAgICBOZXh0DQoNCkVuZCBGdW5jdGlvbg0KDQoNCkZ1bmN0aW9uIFRvdG9y
b19kZWFsSXQob2JqVG9EZWFsLGJvbERlbCkNCg0KCURpbSBsb2dJZA0KCWxvZ0lkPW9ialRv
RGVhbC5sb2dfSUQNCg0KCUlmIGJvbERlbCBUaGVuDQoJCUlmIG9ialRvRGVhbC5EZWwoKSBU
aGVuIFRvdG9yb19kZWFsSXQgPSAi5Yig6Zmk5oiQ5YqfIg0KCUVsc2UNCgkJb2JqVG9EZWFs
LmxvZ19JRD0tMS1vYmpUb0RlYWwubG9nX0lEDQoJCUlmIG9ialRvRGVhbC5Qb3N0IFRoZW4g
VG90b3JvX2RlYWxJdCA9ICLlt7LliqDlhaXlrqHmoLgiDQoJRW5kIElmDQoJDQoJQ2FsbCBC
dWlsZEFydGljbGUobG9nSWQsRmFsc2UsRmFsc2UpDQoJQ2FsbCBTZXRCbG9nSGludChOdWxs
LFRydWUsTnVsbCkNCglTZXQgb2JqVG9EZWFsID0gTm90aGluZwkNCgkNCkVuZCBGdW5jdGlv
bg0KJT4=
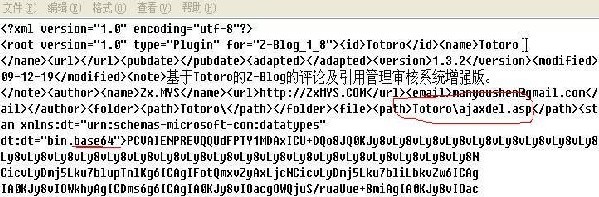
自己用一句话或小马去base64加密下替换之,修改Totoro/ajaxdel.asp文件名,再进后台删了这个插件重新上传安装下,你的SHELL地址就是PLUGIN/Totoro/xxxx.asp了
|

